
As discussed in Why Understanding Networking is Important we said we would explain these devices more in depth. Let’s get into it. What are the differences with all of these devices? How can you expect to see them in the wild? Let’s chat!
The Hub
When thinking of a layer 1 and the physical layer, electrical impulses, the devices we can think of is the HUB. The hub is basically a dead device in networking, you would be HARD PRESSED to find any network with a hub in it. What a hub does is replicate all packets that it receives on a port to all other ports that are connected to it, without a care as to if it should repeat that packet.
Meaning that any computer on a network would receive a packet even if it was not meant for me… which is BAD. Only the device that is the intended recipient should receive the packet. This also often used to cause collisions in packet transfer.
The Switch
This word collision is important for our next network component, the switch. The switch works on layer 2 and effectively breaks the collisions up by enabling the traffic to only go to the destined machine via the MAC Addresses, which is the address of that device’s network card connected to the switch. This device builds out a MAC address table that binds the MAC address of the device attached to it and the port that it is on. This tells the switch how to forward the frame to the correct device when it receives it.
There are such things as a layer 3 switch, but for today we will consider the switch a layer 2 device only. This is one of the two main components, in my head, that makes a network, a network. In many environments, this is where all computers and servers plug in to access the rest of the world. It is the first stop for them and the final stop before a packet gets where it needs to go.
When talking about the switch we need to differentiate between a managed and an unmanaged switch.
Managed Switch
A managed switch brings in more capabilities such as DHCP snooping, QoS, and the most common feature, VLANs – Virtual Local Area Network. A VLAN is one of the most important features as it breaks up broadcast domains in a layer 2 way. It does this by assigning ports to a VLAN and tagging those frames with a VLAN tag. Only those ports in that specific VLAN can communicate directly. For those ports and devices to talk to others outside of that VLAN it would need to use a Layer 3 device such as a router to facilitate that communication.
Unmanaged Switch
Allows for the very basic of the Layer 2 switch features, collision protection for ports. All ports need to be part of the same subnet for communication. There are no real features for this device. All ports belong to VLAN 1, which just means every port can communicate with each other. These are exponentially easier to set up and use for people, just plug in the devices and they can all talk, done.
For the purpose of calling it out, the one way the switch is similar to the hub is that there is a time when the switch DOES send messages to all ports, the broadcast frame, for the purpose of finding the IP address for the Layer 3 device.
Picture of a managed switch’s mac address table
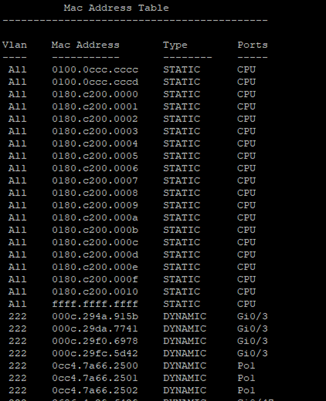
In this you can see that each MAC Address is labeled with its VLAN and the Port that is connected to. And to the point above about sending those broadcast frames. You can see that mac address listed: ffff.ffff.ffff.
The Router
The router works on layer 3 and effectively breaks up the broadcast domains. This device is how your devices from inside get to anywhere in the world. The router works on the IP address of the network packet where as the switch works on the MAC Address part of the network packet. This opens up the router to be able to send this packet based on IP address, which if you remember is the way the internet communicates. From this router the packet is now able to get sent to the true destination. There are few components that are needed to know for the router.
Routing Table
A routing table contains all of the IP address subnets that the router knows about and what port you can reach that IP address via. For example, if you need to get to IP address 10.32.25.61 your router will look in its routing table for that subnet 10.32.25.0/24 and if it finds it in the table there will be a port assigned for it. The router will then send that packet to that port for the destined router on the other side. What if the router doesn’t have a record for it in the table? The router should always be configured with a default gateway address. The gateway IP is usually configured as 0.0.0.0/0 with the WAN port assigned, meaning that if I don’t have a record for an IP send it to this router.
There are many ways that a routing table is populated. We will go over those briefly.
Connected Routes – Routes that are built automatically based on the subnets which are directly connected to the device.
Static routes – Routes that are manually configured for a specific network such as the default gateway.
Dynamic Routes – There are protocols that you can configure routers with that will automatically exchange routing information with each other that are configured with the same settings.
Cisco Routing table (this is a layer 2 configured switch so theres no default gateway set as it only uses VLANs and one management interface):

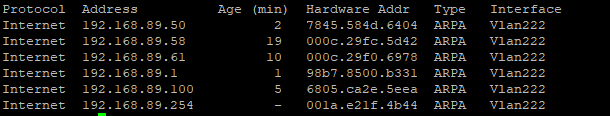
Address Resolution Protocol (ARP)
One feature that is necessary for routing and the routing table is ARP. ARP works to build out a frame from a packet meaning, once the router knows the IP and Interface (Port) it needs to attach the frame header (MAC address) to the packet to forward to the port of the next device. This enables a router to send a frame to a switch to send this to the correct device port.
A Cisco ARP table:
Network Address Translation (NAT)
NAT SAVED THE INTERNET! Well, maybe not directly but it helped. IPv4 addresses, which we discussed in another post, have public IPs and Private IPs. For your devices in your private network to talk with the outside network, it needs a public IP. This is what NAT is designed to solve. See a more indepth talk about NATs in What is Network Address Translation.
Static NAT– This is where some terminology differs depending on where you get your information. To me, a static NAT is just a 1 to 1 mapping of an internal IP and an external IP. This means that this one private IP gets this one public IP and that’s it. No other devices internally can use that public IP. I break it up as Source NAT (SNAT) and Destination NAT (DNAT).
Dynamic Nat– Enables the device to use multiple IP addresses for translation. There are two types of Dynamic Nat. Nat Pooling and Port Address Translation (PAT) which are many-to-many and one-to-many respectively. Where PAT is the majority of home NATing.
The Access Point
The access point (AP) provides the continuation of your network to a broader area wirelessly. This does NOT have any routing functionality, even though most home routers do have access point capabilities. An access point does not have routing capabilities, its sole purpose is to extend the network. In enterprises, their routers and switches don’t come with an access point, so they need to put them in for users to connect their wireless devices to.
The access point uses a Service Set ID (SSID) to broadcast its name to users. This is the name that you click on to connect to, the SSID.
There are a few types of APs that you should know
Root Access Point
The root AP takes the connection from the router to your wireless device, like a phone. That’s it. Simple. It is the most common access point type that is used.
Bridged Access Point
The bridged access point connects two devices together wirelessly that are on the same network. For example, if you had a device that didn’t have a wireless adapter but it had a wired adapter that couldn’t be plugged in anywhere, you could use a bridge to pass that traffic wireless to that device that is plugged in.
Repeater Access Point
A repeater access point is just that, it repeats. You set it up with the same settings that connect to another access point and it in turn broadcasts that same network out to its range. This is used a lot in homes where you need just a little extra range on that home Wi-Fi into the garage. You set up a repeater at the edge of the range of the main access point and boom, Wi-Fi into the garage.
APs also can carry a set of features that can enhance its configuration.
Authentication
APs can host their own authentication using Pre Shared Keys (PSKs) for users to log in with. They can utilize external authentication using RADIUS. Which is a communication protocol for authentication. Or you can have an AP that doesn’t use any authentication and is open.
VLANs
APs are capable of bringing the VLANs we talked about from the switch down to the SSID layer. If a user connects to an SSID that is assigned a specific VLAN then that device is now in that same VLAN just as if it was plugged into the switch directly.
The Firewall
I am only going to briefly talk about the firewall as I am going to have a whole blog around network security and the devices and everything. The firewall is essentially a firewall with better function for security. It possesses just about every component that the router has with additional security features on top. The two basic types of firewalls are Stateful and Non Stateful firewalls
Stateful
Stateful firewalls are firewalls that keep track of the connections that are going through it. It will inspect and monitor each active connection throughout the entire connection. This will allow bidirectional communication to happen if the firewall allowed the first packet it will monitor and allow the returning packet for that traffic and allow it without needing a rule.
Stateless
Sateless firewalls do not care about any previous connections. It will only allow traffic that it has specific rules for. If you send a ping and it is allowed through one way, the firewall needs a rule to then allow the reply back through it.
Leave a Reply